Finding the best deal on an Apple Watch is more than just waiting for an offer and sale; Whether you’re looking at the new series or a budget-friendly model. This article will help you get special discounts and regular models, so you can get the smartwatch you want without spending.
Table of Contents
Apple Watch Deal Cycle: A Yearly Pattern
Apple Watch pricing follows a clear annual pattern. Understanding this series is the first step to strategic shopping.
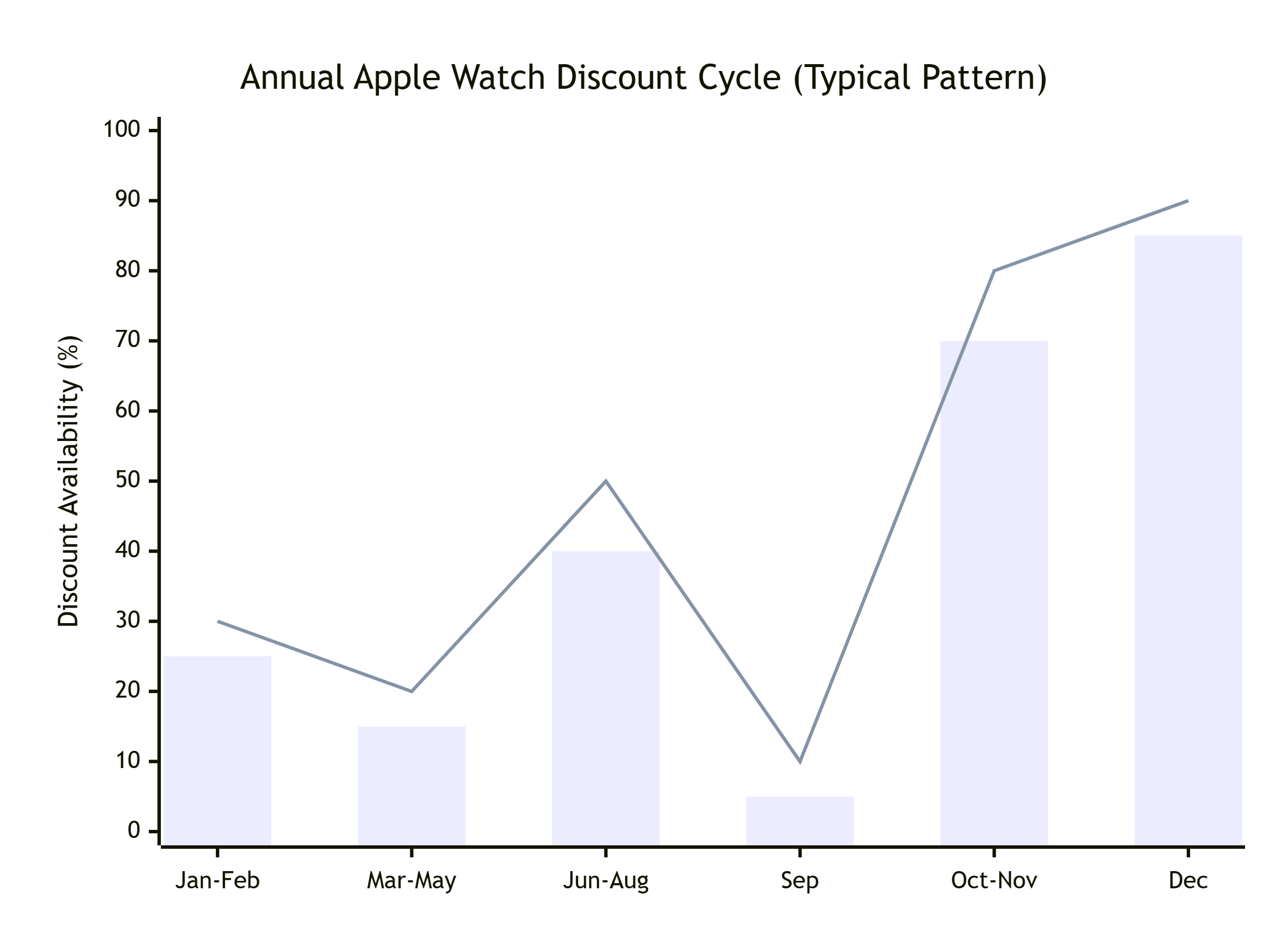
Key Takeaway: The easy discounts usually ensue right after new model announcements (Sep-Oct) on earlier generations, and during main holiday sales (Nov-Dec).
Current Apple Watch Pricing
| Apple Watch Model | Starting Price (New) | Typical Deal Price Range | Best For |
| SE | $249 | $179 – $219 | First-time buyers, budget, essentials |
| Ultra 2 | $799 | $699 – $749 | Athletes, longest batter, adventurers |
| Series 8 | Discontinued | $249 – $299 | Value seekers |
| Series 9 | $399 | $299 – $349 | Double Tap, Latest features, brightest display |
Note: Stainless Steel and Hermès editions command higher prices with less frequent discounts.
Where to Find the Best Apple Watch Deals: Location & Retailer Strategy
Official Apple Channels
- Apple Renewed Store:The best standard for certified renewed devices. Smartwatches include a new battery, shell, and a full 1-year warranty.
- Education Store:Yearly discount for teachers, students, and staff. Usually $20-$50 off watches.
- Trade-In Program:Directly going through Apple can reduce your price, though third-party sites often offer more money.
Major Retailers (Best for New Models)
| Retailer | Typical Discounts | Best Timing | Considerations |
| Amazon | Daily deals, Prime Day, Black Friday | Prime Day (July), Black Friday | Check seller is “Amazon.com” or authorized |
| Walmart | Rollback pricing, Black Friday specials | Black Friday, November | May have older stock at deep discounts |
| Best Buy | Open-box deals, Black Friday, My Best Buy member pricing | Black Friday, post-holiday clearance | Open-box “Excellent” condition can save 10-15% |
| Target | Circle offers, gift card with purchase | Holiday season, Target Circle Week | Bundle deals (gift cards) add value |
Carrier Deals
- Verizon, AT&T, T-Mobile:Offer “free” Apple Watch with new line or important discounts with 24–36-month installment plans.
- Catch:Needs cellular plan ($10-$15/month), joining you to a lengthy contract. Best for those already requiring a new plan.
Alternative Marketplaces
- eBay:Look for Apple Certified Renewed sellers or open box returns. Pro tip: Filter by Seller renewed with warranties from reliable electronics renews.
- Swappa, Gazelle: Markets with Apple Watch rating. Generally safer than Facebook Marketplace.
Strategic Timing: When to Pull the Trigger
- September-October:New Apple Watch model statement leads to immediate retailer price on previous models.
- Black Friday / Cyber Monday:Broadest retailer participation. Expect $50-$100 off the newest models, lower cuts on older stock.
- Prime Day (July):Amazon, but other retailers match. Good for SE and previous-gen Series deals.
- December Post-Holiday:Clearance on overstocked configurations and holiday returns.
- March-May:Slower sales cycle can produce unexpected open-box or allowance finds.
Smart Comparisons & Alternatives
Should You Buy the Latest Model?
Considering previous generations, the Series 8 remains a qualified watch, often found at considerable discounts. The performance difference between Series 8 and Series 9 is minimum for most customers.
Apple Watch SE vs. Series 9: Is the Upgrade Worth It?
| Feature | Deal Hunter Verdict | Apple Watch SE (2nd Gen) | Apple Watch Series 9 |
| Always-On Display | Major differentiator | No | Yes |
| Blood Oxygen & ECG | Health-focused users need Series | No | Yes |
| Fast Charging | Nice but not essential | No | Yes |
| Double Tap Gesture | Convenient, not crucial | No | Yes |
| Typical Deal Price | SE offers best pure value | $179-$219 | $299-$349 |
Verdict: If Always-On Display and advanced health sensors aren’t critical, the Series at under $200 is arguably the best value in smartwatches today.
Non-Apple Alternatives to Consider on a Tight Budget
- Fitbit Charge 6: For basic fitness tracking and notifications ($160).
- Samsung Galaxy Watch 6: Best Android alternative, frequent discounts ($250-$300 on sale).
- Amazfit/Coros: Excellent battery life for dedicated fitness tracking ($100-$200).
Location-Specific Tips
- United States:Leverage retailer-specific credit cards and membership programs.
- United Kingdom:Check John Lewis for extended warranties (2+ years included). Amazon UK and Currys have strong seasonal sales.
- Canada:Best Buy Canada and The Source often have approval events. Watch for Amazon Prime Day concurrent with US.
- Australia:JB Hi-Fi has reasonable bundles and gift card offers. Harvey Norman can negotiate in-store.
- Europe:MediaMarkt and FNAC run forceful promotions, especially post-New Year.
Pro Tips for Guaranteed Savings
- Use Price Tracking Tools:Set alerts on Camel (Amazon), Honey, or Keepa to monitor old lows.
- Check Apple’s Renewed Stock Daily:Inventory changes normally. Models in “Like New” restriction appear regularly.
- Consider Certified Renewed from Authorized Sellers:Best Buy Open-Box Excellent and Amazon New Premium offer near-new quality with solid warranties.
- Bundle with Gift Card Promotions:Sometimes a “$50 gift card with purchase” offers more give than a straight discount.
- Don’t Fear Last Year’s Model:The Apple Watch Series 8 is 95% as qualified as the Series 9, often at a 30% discount.
Conclusion
- Timed my purchasewith the seasonal cycle
- Checked refurbishedoptions from Apple & authorized sellers
- Compared trade-in valuesbetween Apple and third parties
- Set price alertsfor my chosen model
- Verified compatibilitywith my iPhone iOS version
- Considering my real needs
The best Apple Watch deal ensures consistent timing, retailer selection, and model selection. By focusing on the previous-generation Series watches during permission periods, you can protect premium Apple ecosystem advantages at very budget-friendly prices. Endurance and research constantly pay off in the smartwatch market.