Table of Contents
What is Two Factor Authentication?
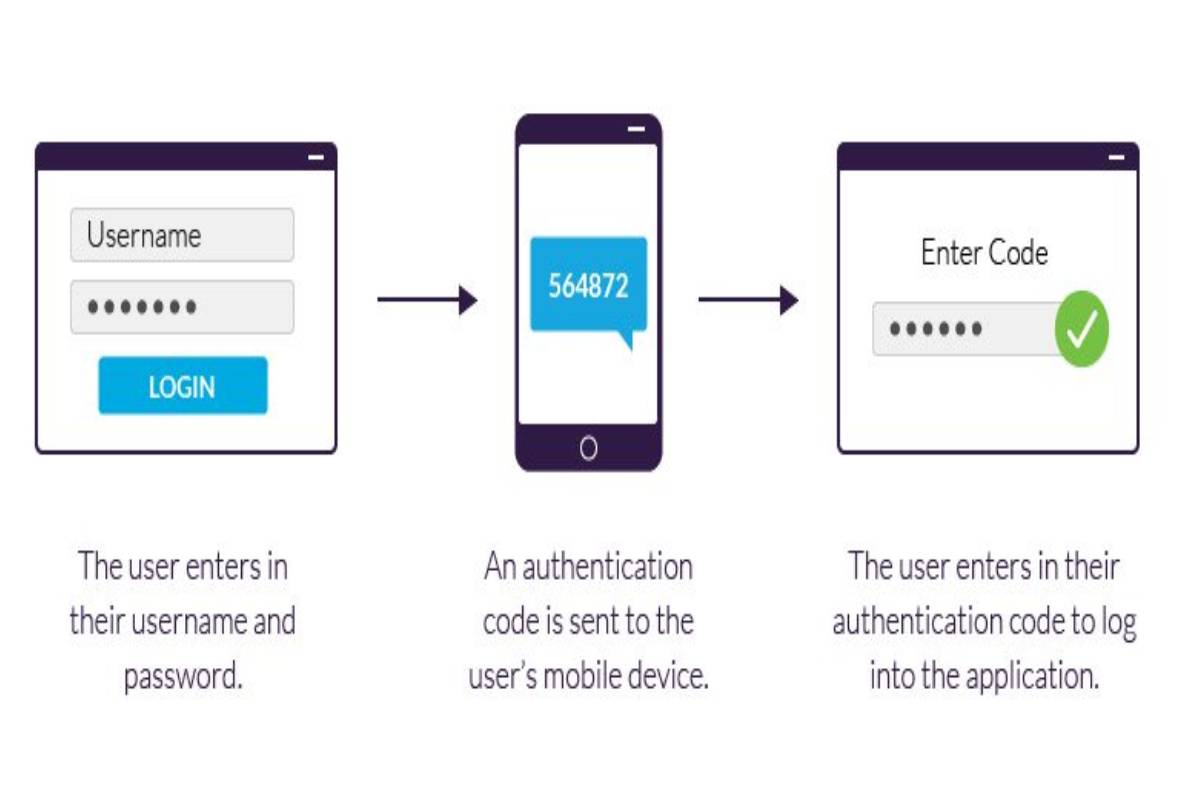
- A Two Factor Authentication is a tool offered by several online service providers, which serves the purpose of adding a layer of security to the login process of your Internet accounts.
- The mechanics are simple: when the user logs in to his online service account, this tool asks him to authenticate the ownership of his performance, providing two different factors.
- The first of these is the password. The second can be several things, always depending on the service.
- In the most common of cases, it is usually a code sent to a mobile phone via SMS or to an email account.
- The fundamental essence of this tool comes down to the fact that you must “know something” and “own something” if you want to log into one of your accounts.
Methods
- While two-factor authentication is not a foolproof method, it is an excellent barrier to preventing unwanted intrusion into your online accounts.
- What is Knwoledge Management System (KMS): It is public knowledge that passwords have a double edge:
- The weakest are easy to remember but very easy to deduce.
- And the strong ones can be difficult to guess, but they are also challenging to remember.
- Thus, many people, who are not already good at creating strong passwords, use the same password for all their accounts.
- In this sense, two-factor authentication essentially achieves that an attacker has to decrypt the user’s password and access a second factor.
- It is much more difficult to obtain, and that would involve either stealing a cell phone or compromising an email.
Best Secure System
- Client Management System: If the two-factor authentication system is secure, then it is the best protection you can have in these cases.
- There is a second benefit that this tool provides, and that is that it lets you know when someone has tried to enter your account without authorization.
- If you receive a code to access your account on your mobile or in your email and you were not the one who tried to log in.
- It is because someone has guessed your password and wants to enter your profile.
- If this happens, you must change your password immediately.
In which accounts should you activate Two Factor Authentication?
- The rule is simple. If the service you use offers a Two Factor Authentication tool and that account is valuable to you.
- You should activate it.
- In simple words, the priorities should be your online bank accounts, your email.
Are there other forms of two-factor authentication?
- In addition to mentioned, there are tools as RSA’s Secure ID, a generator of chained codes and is typically using in the corporate sector.
- Along with the previous ones, are the most used, although there are still more:
- The Transaction Authentication Number (TAN) is an old form of two-factor authentication used in the past.
- They were popular in Europe, and it was in the following way:
- Your bank would send you a list of TAN’s and every time you had to make a money transaction, you had to enter one of these codes.
- The ATM also works as a two-factor authentication tool, like something you must “know” -your PIN- and something you must “have” -your debit card.
- Currently, many companies implement biometric technologies that serve the same functions.
- Some systems require a personal password, scanning the fingerprints, the pupils, or even the users’ heartbeat.
- On the other hand, wearable devices are catching on as well.
- Some systems require that you wear a unique bracelet or some other accessory with a built-in chip.
- Some scientific papers already speak of electromagnetic tattoos that could be helpful for these same purposes.
- Google and Facebook have their applications to generate codes.
- It allows users to create their unique access codes instead of receiving them by SMS or email.
Also Read: Apple Mini – Definition, Specifications, Ideal Choices, and Reviews
- KNOW MORE:- smartmores

Review Two Factor Authentication – Definition, Method, Steps, Forms, and More.