Table of Contents
Introduction
Mobile apps play a life-threatening role in digital business models. It especially involve in e-commerce, fintech, healthcare, education, and on-demand services. As per user expectations and experience it rise and intensifies the competitors and delivering a bug-free app. It also gives high-performing mobile app.
The Outsourcing mobile app testing permits organizations to ensure quality, reduce costs, and time-to-market. This method is gradually adopted by startups, SMEs, and enterprises.
Why Mobile App Testing Is Critical
Mobile app testing ensures:
- Cross-device compatibility
- Security and data protection
- Performance under load
- Functional correctness
- Positive user experience
Any failure in these areas can directly impact customer trust and revenue.
Yearly Industry Growth Context
(E-commerce Marketing Strategy Trend – Indicative)
The growth of E-commerce Marketing Strategy directly impacts mobile app quality requirements, as most e-commerce traffic now comes from mobile apps.
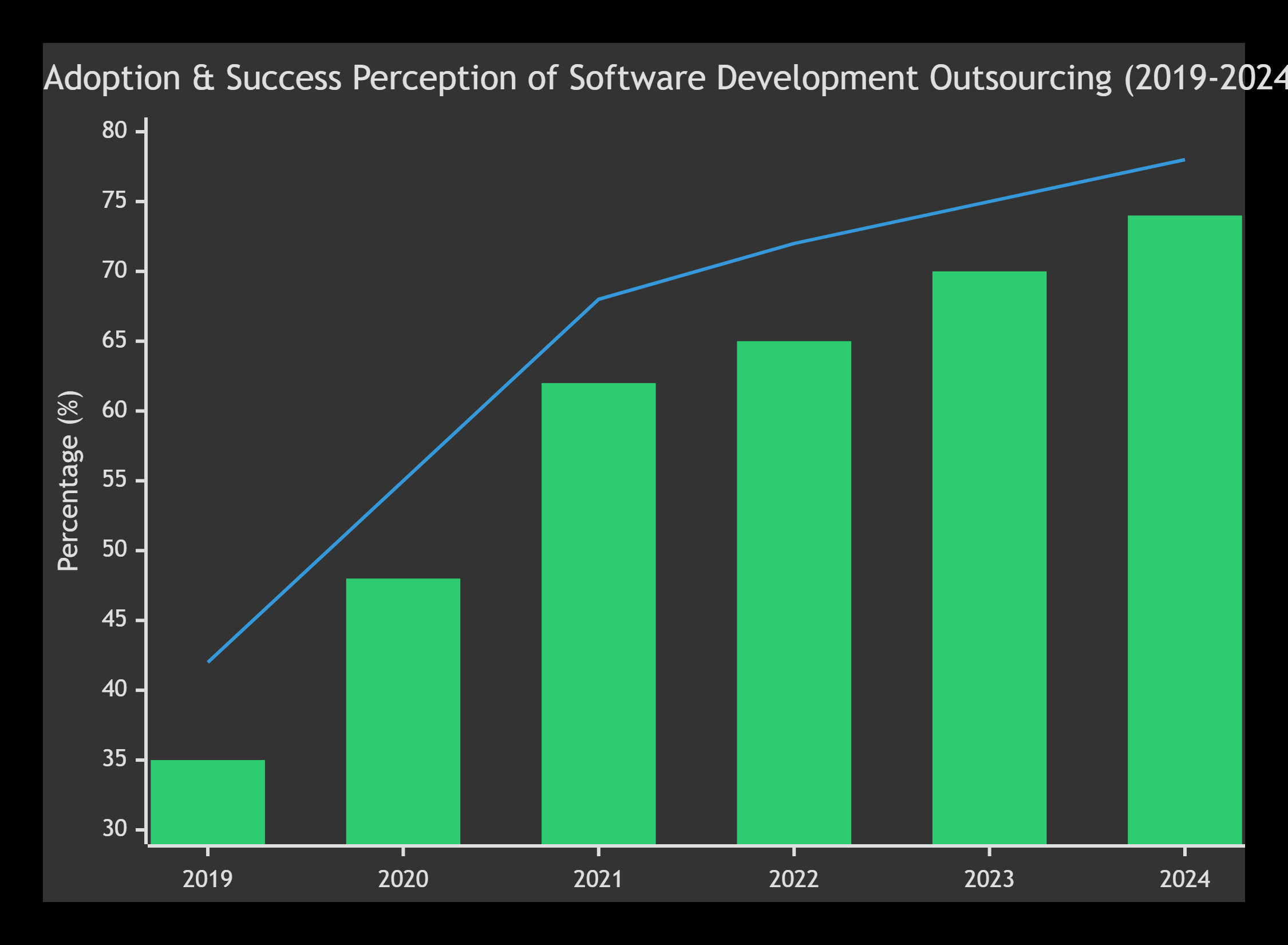
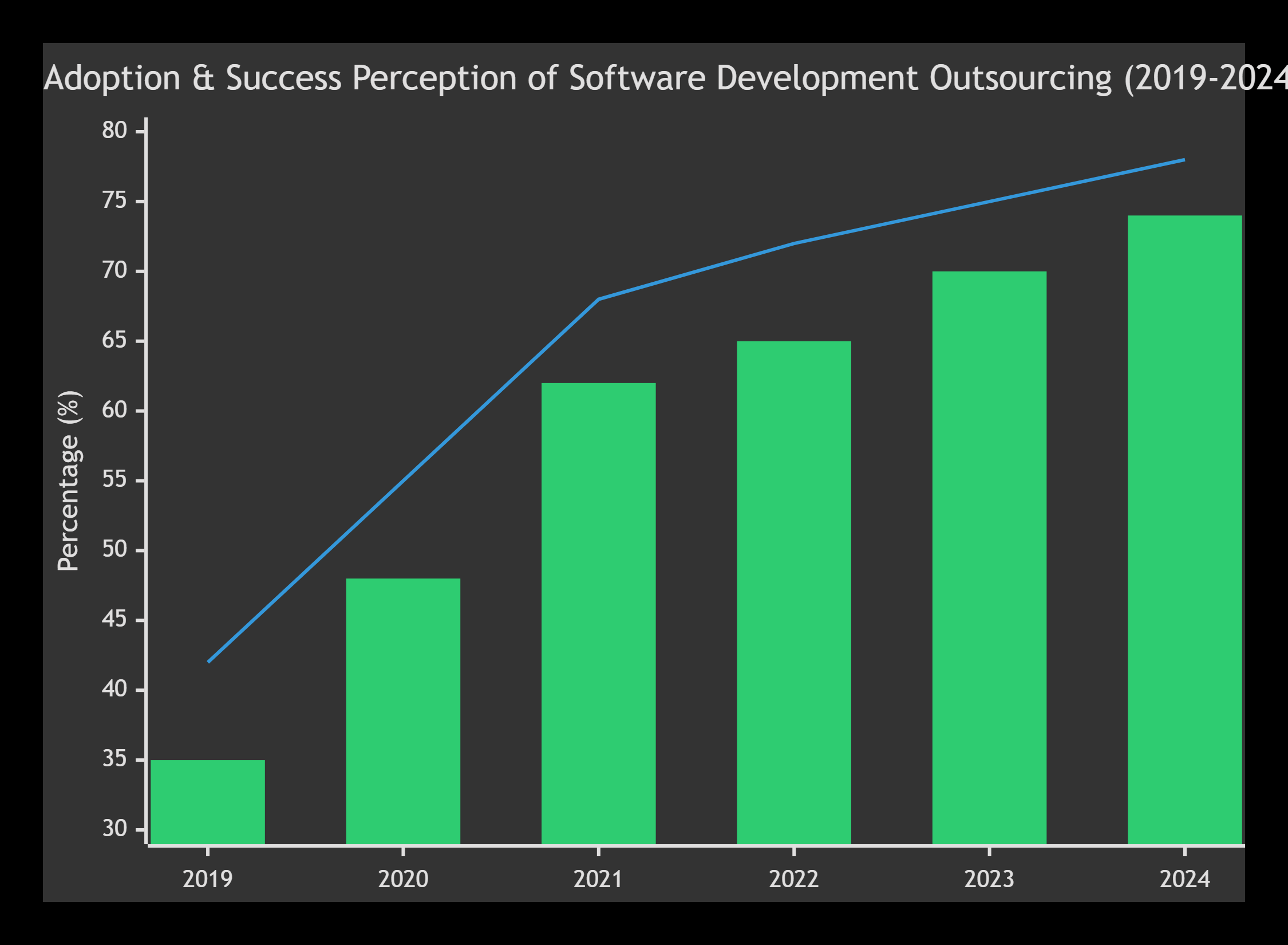
Yearly Search Interest Index
| Year | Search Interest Index |
| 2020 | 45 |
| 2021 | 60 |
| 2022 | 75 |
| 2023 | 90 |
| 2024 | 105 |
| 2025 | 120 |
As marketing expands, mobile apps must perform flawlessly—driving demand for outsourced mobile app testing services.
Top Reasons to Outsource Mobile App Testing
-
Cost Efficiency
Outsourcing removes expenses related to hiring, training, infrastructure, and testing tools.
-
Access to Skilled Testing Experts
- Manual and automated testing
- Security testing
- Performance and load testing
- Device and OS compatibility testing
-
Faster Time-to-Market
Dedicated outsourced teams work in parallel with development, reducing release cycles.
-
Scalability and Flexibility
Testing efforts can be scaled up or down based on project requirements.
-
Access to Real Devices and Tools
Outsourcing providers maintain extensive device labs and licensed testing tools.
Pricing of Outsourced Mobile App Testing
Average Cost Structure
| Engagement Model | Estimated Cost |
| Hourly Model | $15 – $50/hour |
| Dedicated Team | $2K – $10K/month |
| Project-Based | $1K – $20K+ |
Cost Comparison
| Factor | In-House Testing | Outsourced Testing |
| Hiring Cost | High | None |
| Tool Licensing | Expensive | Included |
| Scalability | Limited | High |
| Time to Start | Slow | Immediate |
Comparisons & Alternatives
Outsourcing vs In-House Mobile App Testing
| Aspect | Outsourced Testing | In-House Testing |
| Cost | Lower | Higher |
| Expertise | Specialized | General |
| Infrastructure | Provided | Self-managed |
| Flexibility | High | Low |
| Long-term Control | Medium | High |
Alternatives to Outsourcing Mobile app
| Alternative | Best Use Case |
| Crowdsourced Testing | UX and real-user feedback |
| Automated Testing Tools | Regression testing |
| Hybrid Model | Partial in-house control |
| Freelance Testers | Small projects |
Location-Based Outsourcing Considerations
Location impacts pricing, communication, and delivery timelines.
| Region | Key Advantage | Cost Level |
| North America | High quality, same time zone | High |
| Europe | Strong compliance standards | Medium–High |
| Asia (India, Philippines) | Cost-effective, skilled talent | Low |
| Eastern Europe | Strong technical expertise | Medium |
| Latin America | Time zone alignment with US | Medium |
Many companies choose a hybrid model—strategic oversight locally with testing execution offshore.
Industries That Benefit Most
| Industry | Testing Focus |
| E-commerce | Performance & checkout |
| On-demand Services | Load & real-time performance |
| Fintech | Security & compliance |
| Education | Device compatibility |
| Healthcare | Data privacy & accuracy |
Conclusion
The Outsource mobile app testing is a tactical decision that helps businesses to deliver high-quality applications. It also control costs and accelerate releases. The growth of e-commerce marketing enhance professional testing. It has converted a necessity rather than an option.
By understanding assessing models, comparing alternatives, and picking the right outsourcing location, organizations. This can confirm its reliable, scalable, and user-friendly mobile applications.